Secure IoT Access: Best SSH Practices On AWS
Are you grappling with the complexities of remotely accessing your IoT devices, navigating firewalls, and ensuring robust security in the AWS cloud? The effective and secure management of Secure Shell (SSH) connections is not just a technical detail, but a critical cornerstone for the success of your IoT deployments, offering a potent blend of control, security, and flexibility.
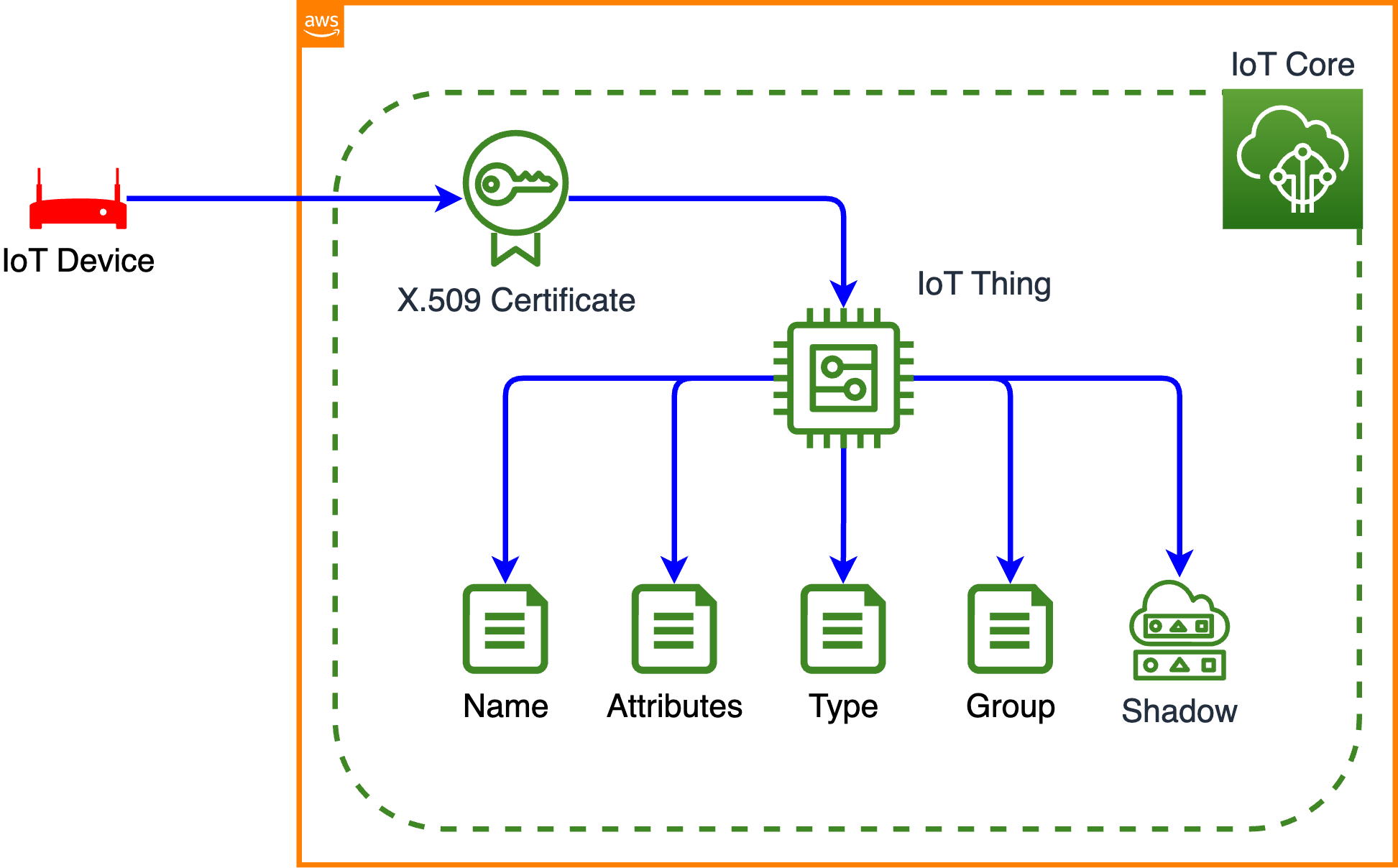
In the burgeoning landscape of the Internet of Things (IoT), the ability to remotely access and manage devices deployed across various locations is paramount. This capability unlocks a multitude of opportunities, from proactive maintenance and troubleshooting to seamless software updates and real-time data monitoring. However, the inherent challenges in securing these remote connections, especially when dealing with devices behind firewalls and with public IP addresses, can be daunting. This is where SSH, or Secure Shell, steps in as a powerful solution. SSH, a cryptographic network protocol, provides a secure channel for communication over unsecured networks, ensuring that data transmitted between your IoT devices and the cloud remains encrypted and protected from unauthorized access. It essentially acts as a secure tunnel, allowing you to remotely access your devices as if you were physically present.
This article delves deep into the strategies, tools, and best practices for achieving the best SSH to IoT device AWS setup. We will explore the essential aspects of managing SSH for IoT devices, from understanding the basics of SSH to setting up your devices and following best practices. Our aim is to equip you with the knowledge and insights needed to keep your IoT ecosystem secure and efficient.
| Key Considerations for Secure SSH to IoT Devices on AWS | Details |
|---|---|
| Authentication | Implement Public Key Authentication: Replace password-based authentication with public key authentication. This significantly enhances security, as public key authentication is far less vulnerable to brute-force attacks. |
| Root Login | Disable Root Login: Disable root login to prevent unauthorized access to the system's most privileged account. This minimizes the attack surface and prevents potential attackers from gaining complete control over your devices. |
| Firewall Configuration | Configure AWS Security Groups and Device Firewalls: Configure the AWS security groups and device firewalls to restrict SSH access to only trusted IP addresses or networks. This limits the exposure of your devices and protects them from unauthorized access attempts. |
| SSH Port Configuration | Change the Default SSH Port: Change the default SSH port (port 22) to a non-standard port. This can help obfuscate your SSH service and deter automated scanning and attacks. |
| Regular Updates | Keep Software Up-to-Date: Regularly update the SSH server software and the operating system on your IoT devices. This ensures that you are protected from known vulnerabilities and security exploits. |
| Monitoring and Logging | Enable SSH Logging and Monitoring: Enable detailed SSH logging to monitor for suspicious activity, such as failed login attempts or unauthorized access attempts. Consider integrating these logs with a security information and event management (SIEM) system for advanced analysis and threat detection. |
| Two-Factor Authentication (2FA) | Implement 2FA: For enhanced security, consider implementing two-factor authentication (2FA) for SSH access. This adds an extra layer of security by requiring a second form of verification, such as a one-time password (OTP), in addition to the user's credentials. |
The ability to remotely SSH to IoT devices on AWS has numerous applications across various industries. For instance, farmers can remotely monitor and control irrigation systems, ensuring optimal water usage and crop health. This remote access capability can be a game-changer for various sectors, optimizing operations and enhancing efficiency.
One of the primary challenges in remotely accessing IoT devices is navigating the firewalls that often guard them and the complexities of their publicly shielded IP addresses. With the increasing number of IoT devices deployed, the need for secure and reliable remote access solutions becomes even more critical. SSH is not just a convenience; it is a necessity for secure and efficient management. Connecting to IoT devices securely using SSH through AWS is a crucial task for developers and system administrators alike. AWS provides the infrastructure, while SSH ensures that your connections are encrypted and safe from prying eyes.
Let's delve deeper into the practical aspects of setting up and optimizing SSH for your IoT devices on AWS, starting with the foundational understanding of SSH itself.
SSH, or Secure Shell, is a cryptographic network protocol designed to establish a secure channel for communication over an unsecured network. It does this by encrypting all the data transmitted between the client and the server, ensuring that even if the network is compromised, the data remains protected. This encryption is critical, especially in IoT environments where sensitive data may be transmitted between devices and the cloud.
When it comes to IoT devices hosted on AWS, SSH ensures that data transmitted between the device and the cloud remains encrypted and protected from unauthorized access. By using SSH, you can securely manage your devices, troubleshoot issues, and deploy updates, regardless of their physical location.
To optimize SSH for IoT remote access on AWS, it is essential to consider the following best practices. Employing these measures enhances security and ensures the efficient operation of your remote access setup:
Use public key authentication instead of passwords for enhanced security. This is a fundamental security measure. Public key authentication relies on cryptographic keys, making it significantly more resistant to brute-force attacks than traditional password-based authentication.
Disable root login to prevent unauthorized access. By disabling root login, you prevent attackers from directly accessing the system's most privileged account. This minimizes the attack surface and enhances the overall security posture of your IoT devices.
AWS offers several methods for setting up SSH access to your IoT devices. One of the most common methods involves using the AWS EC2 instance as a jump host or bastion host. The setup can be manual or automated, offering various levels of flexibility and control. For instance, the manual setup method involves configuring the EC2 instance, setting up SSH keys, and configuring security groups to allow SSH traffic.
For an example that shows how to open a tunnel using the manual setup method, see "open a tunnel using manual setup and connect to remote device." This example demonstrates the step-by-step process of establishing a secure tunnel, allowing you to connect to your IoT devices securely. Quick and manual setup methods; criteria quick setup manual setup; create a new tunnel with default, editable configurations.
To access your remote device, you can only use SSH as the destination service.
Securing your IoT infrastructure is paramount. With the increasing number of IoT devices being deployed, the need for robust security measures is more critical than ever. SSH plays a pivotal role in this, providing a secure means of managing and accessing your devices.
In essence, SSH for IoT on AWS is more than just a technical solution; it's a strategic approach to ensuring the security, manageability, and efficiency of your IoT deployments. By understanding the basics of SSH, implementing best practices, and leveraging the power of AWS, you can create a robust and secure IoT ecosystem.
This article has explored the best practices, tools, and configurations for establishing secure SSH connections to IoT devices on AWS. We have discussed the essential aspects of managing SSH for IoT devices, from setting up SSH on AWS to optimizing performance and ensuring compliance. The goal is to provide you with a comprehensive guide to the best SSH practices for connecting to IoT devices on AWS. We've covered everything you need to know to keep your IoT ecosystem secure and efficient.
The key is to remember that SSH is not a set-it-and-forget-it solution. Continuous monitoring, regular security audits, and staying informed about the latest security threats are essential for maintaining a secure IoT environment.
By following these guidelines and leveraging the tools and services offered by AWS, you can effectively manage SSH connections to your IoT devices, ensuring secure remote access, streamlined management, and robust security. This allows you to focus on the core functionality of your IoT applications and unlock the full potential of your IoT deployments.

Best Remote SSH IoT Device AWS A Comprehensive Guide

IoT SSH Download AWS The Ultimate Guide To Securely Accessing Your Cloud Resources
Unlocking Secure IoT SSH Access On AWS A Comprehensive Guide